Configure your router to watch for login attacks.
Even though we can configure SSH for secure management, this still does not stop a random person from connecting to your device in an attempt to guess the password. In some cases this could be a bored user who is just curious or in worst cases it could be a malicious user trying to perform a dictionary attack on your password. Something we can do is to configure our router to start blocking login request after so many failed attempts occur within a specific time frame. Now this isn’t going to secure your router indefinitely but it is a simple preventative measure they will slow down any real dictionary attacks and will most likely discourage any bored employees in hopes that they lose interest or remember they have other work to do.
So now let’s say we have an existing router with SSH enabled and we want to configure this login block feature, well let’s enter the following command:
Yep one command. This will block all logins for 120 seconds when 5 failed attempts occur within 60 seconds of each other. Below is a breakdown of the block-for command, and notice all the timers are in seconds.
Now when the router notices these failed attempts it enters a “quiet mode”. This quiet mode is what tells the router to block all further login attempts until the timer expires.
So now I hit my router with a bunch of invalid attempts and noticed the following error get logged:
This message states quiet mode is now on and also notice it actually logs the username I attempted to log in as (ss in this case), the source of the login attempt (192.168.1.109), the port I connected on (22 default for SSH), and the reason (failed login authentication)
From this point I cannot even connect to the router over port 22, putty flat out tells me the connection is refused:
The following error message will also get logged when I attempt to login to a router that is currently in quiet mode:
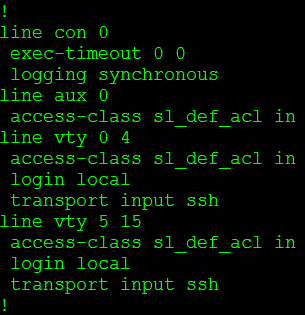
Stating our login attempt has been blocked by an ACL, but wait we didn’t configure an ACL on this router. Let’s check the VTY lines:
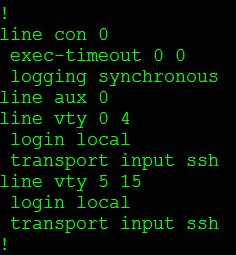
We didn’t configure this ACL but the login block feature did. The cool thing about this is when “quiet mode” is turned off the ACL dissappears:
Pretty cool right? We have now taught the router to protect itself.
While this is a nice feature to have configured the last thing you want is to find yourself locked out of your own equipment. So what we can do is configure the router to accept login attempts even when quiet mode is enabled, while that might sound counter-productive to this whole feature it will be something you definitely want to do.
And we do it this way:
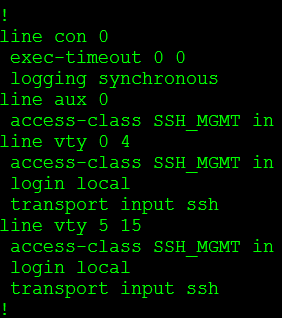
The first thing I did was create an ACL (SSH_MGMT) that permits my management workstation (or management subnets) and then I issue login quiet-mode access-class command and reference the ACL I created. This tells the router to accept login requests from the hosts allowed within the quiet-mode ACL when quiet mode is on and the router is blocking login attempts from everyone else.
So now when quiet mode is initiated this custom ACL is applied to the line VTY lines:
You can verify your configuration with the show login command, this provides you a nice summary of what has been configured as well as the current state of the router:
A few things to keep in mind:
- While the quiet mode ACL will allow login attempts from hosts matched in the ACL, those very same hosts can trigger the router to enter quiet mode.
- If you already have an access-class assigned to the VTY lines and quiet mode kicks in, the quiet mode ACL will be applied during the block-for time. However when the timer expires the quiet mode ACL is removed and the original ACL back in place.








I see a lot of interesting posts on your website.
You have to spend a lot of time writing, i know how to save you
a lot of work, there is a tool that creates unique, google friendly articles in couple of minutes, just
type in google – k2 unlimited content
Rufus
July 16, 2014 at 6:52 PM
So what would be the end effect of a person brute forcing your router or switch login? What this effectively prevent any logins. So, for example, as I brute force attempt to discover the password, I’ll get locked out for 120 seconds and then my script will continue to run. After 120 seconds and then the next five failed, I would get locked out again? Would this not effectively render the switch or router in a lockout loop of sorts so not even legitimate users could login? Or, as long as I log in from a different host, I’m okay since it logs the source IP address. I may have just answered my own question.
B Drew
May 1, 2017 at 11:16 PM
Correct, as long you specify an access list for the ‘quiet mode’ configuration and attempt to connect from that configured network, you still have access to the router. While anyone not allowed in the quiet mode ACL will continue to be denied.
This just designed to be a deterrent, since it can cannot stop the attack from continuing. This can however alert you to the incident with additional logging and alerting on your syslog server. This can provide valuable time to investigate the issue.
Stephen J. Occhiogrosso
May 2, 2017 at 6:19 AM
“If you already have an access-class assigned to the VTY lines and quiet mode kicks in, the quiet mode ACL will be applied during the block-for time. However when the timer expires the quiet mode ACL is removed and the original ACL back in place.”
So if I already have an ACL and access-class assigned to VTY lines to only allow login from the host address I specify, then that ACL and access-class will be replaced by quiet mode ACL if x number failed attempts from the allowed host address?
I’m assuming the quiet mode ACL will be removed after the block-for-time has expired and my configured ACL and access-class will be re-applied?
So this would config the router so x number of failed logins from the host address I already specified would trigger quiet mode and apply the newly configured quiet mode ACL (same allowed host IP address)?
Paddy
May 31, 2021 at 11:11 AM