You don’t have to block ICMP completely.
This is something that I typically see all over the place, security administrators blocking the ICMP (Ping) protocol completely. Normally I am ok with that, after all ping is a troubleshooting tool and in some cases not the best troubleshooting tool to rely on. However, it’s when people think their network is more secure when they have blocked ICMP. The truth is you can actually allow the ICMP types that are required for troubleshooting purposes without compromising security. So let’s first consider what ICMP messages we typically use for troubleshooting:
- Echo Request – ICMP Type 8 Code 0
- Echo Replies – ICMP Type 0 Code 0
- Time Exceeded – ICMP Type 11 Code 0
- Fragment needed but DF bit set – ICMP Type 3 Code 4
Now we all know the echo request is the icmp packet from the host to the target, and the echo reply is response from target back to the host. The time exceeded packet is returned to the host when performing a traceroute. The fragment needed but DF bit set packet is used for path MTU discovery and can used to troubleshoot MTU issues, it basically replies back telling you the packet was dropped because it needed to be fragment but the DF (Do not fragment) bit was set on the packet so it could not be fragmented.
One ICMP parameter that should be blocked are ICMP fragments, fragmented ICMP packets can be used to cause DoS attacks. Remember ICMP packets typically send 64 bytes of data, so you should only see larger ICMP packets or expect fragments when testing MTU. (Other then that I can’t think of any other legit reason to see large ICMP packets). RFC 1858 goes pretty in depth concerning the danger of IP Fragments, it’s definitely worth a read.
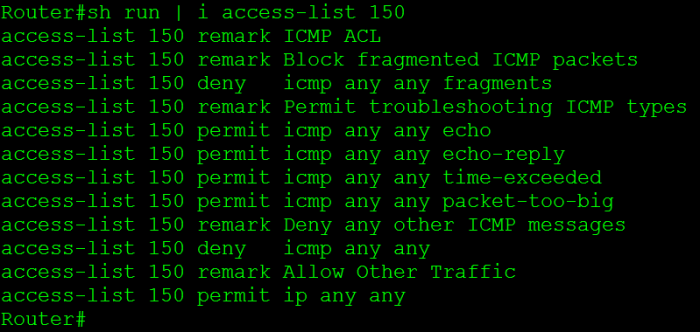
Now here is a configuration snippet that accomplishes everything I discussed here:
Now if you want to learn about ICMP in greater detail check out RFC 792.

Hi Stephen,
Good article. With IPV6 things have changed a bit, since ICMPv6 packets are used for discovering neighbors and routers. See http://www.ietf.org/rfc/rfc4890.txt on what ICMPv6 messages need to be
allowed for things to function correctly using IPV6.
Steve Clark
March 6, 2012 at 12:25 PM
Cool, thanks for the link Steve ICMPv6 will probably be getting its own post in the future. Lots of new things to go over & learn with the new protocol!
Stephen J. Occhiogrosso
March 6, 2012 at 11:25 PM
I am not security expert, but going through similar crisis. Does blocking ICMP/Ping on public network and not on private really protect your network or make it harder for any hacker to scan your network? Please advise.
Randy
June 27, 2017 at 3:33 PM